[Note: This is part 2 of a 3-part blog post on Nuage Networks release 4.0. Part 1 | Part 3]
Continuing our series on major enhancements in Nuage Networks release 4.0, in this post we explore major security enhancements in the new Virtualized Security Services component of the VSP architecture.
Virtualized Security Services (VSS): Software Defined Security for DC and WAN
Nuage Networks is delivering a new software defined security offering called Virtualized Security Services (VSS) that is based on several new security capabilities introduced in 4.0, in addition to security capabilities earlier in VSP 3.x releases. VSS is the industry’s first distributed, end-to-end (cloud, DC, branch) software-defined network security, visibility and security automation solution.
VSS allows organizations to:
- Prevent security incidents by minimizing attack surface with software-defined segmentation and policy enforcement across cloud, data center and branch
- Detect security threats and monitor compliance with contextual network visibility and security analytics
- Respond in near real-time to incidents by dynamically automating security remediation processes
VSS Prevent: Segmentation and Distributed Security Policy Enforcement
VSS Prevent enables software-defined end-to-end network segmentation for controlling access to any workload from branch networks as well as from within the data center.
Inside the datacenter, VSS provides microsegmentation for any workload (VM – multi-hypervisor, containers, bare-metal). VSS distributed firewall enforces Layer 4 stateful ACLs as well as service chaining policies (e.g., NGFW, IPS). Beyond data center, VSS also provide software-defined fine-grained segmentation and policy enforcement across branch and datacenter. Layer 4 stateful ACLs can be used for better security at branch perimeter to restrict user access at the branch. For example, access to corporate network as well as data center can be restricted to guest users.
Layer 4 stateful ACLs is a new feature added in the 4.0 release. Layer 4 Stateful ACLs track connection state based on IP header as well as Layer 4 transport protocol, to help detect valid connections, and incorporate connection state into access policy decisions (e.g., tracking TCP connection using TCP SYN/RST flags to terminate invalid or incomplete connections like SYN flood). This helps provide more secure microsegmentation in the datacenter, as well as better branch perimeter security with Layer 4 traffic filtering to/from the outside network.
In addition, Nuage Networks has validated that the end-to-end segmentation with distributed firewall using the Layer 4 stateful ACLs capability meets the network segmentation requirements for PCI-DSS (Payment Card Industry Data Security Standard) and can be used to reduce scope of PCI compliance across both the data center and WAN.
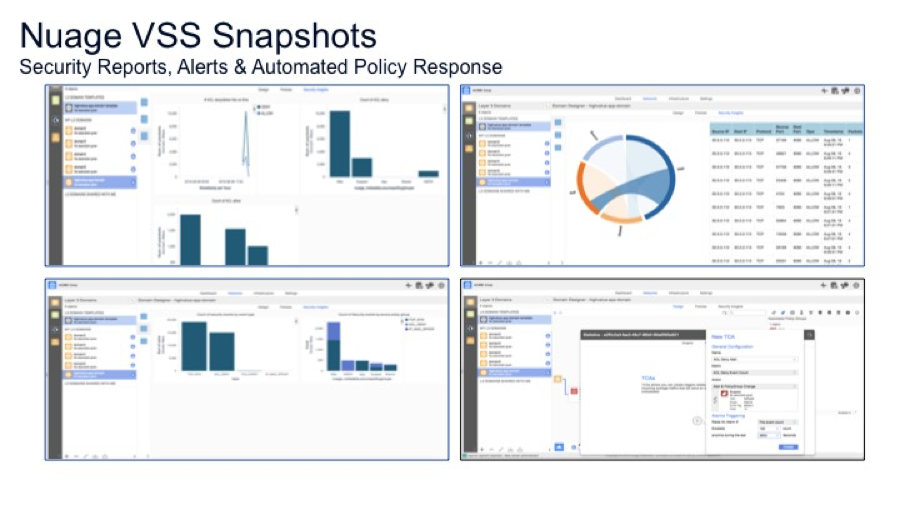
VSS Detect: Visibility and Security Monitoring
VSS allows customers to visualize traffic flows with SDN context both within the datacenter as well as between datacenters and branch networks for auditing compliance with Infosec policies. Application flow mapping based on contextual flow visualization (e.g., Layer 4 protocol/ports information used by flows between application components/policy groups) enables auditing and definition of whitelist security policies for microsegmentation.
VSS provides security monitoring capabilities with new security dashboards and near real-time alerts based on ACL as well as traffic analytics. Examples of security dashboard reports include:
- ACL deny / allow count vs. time
- Security events by source/dst policy groups, zone
- Top sources causing ACL denies
- Top talkers in the virtual network
VSS also provides new policy-based mirroring of select traffic to security analytics/IDS systems for enhanced analysis. Only traffic that matches a defined policy will be mirrored, so users can be selective about what they choose to analyze and not overwhelm the system. For example, users can choose to mirror traffic to specific ports from external sources matching ingress/egress ACL policies.
VSS Respond: Dynamic Security Automation
Release 4.0 introduces new powerful feature that enables network security administrators to define threshold crossing alerts (TCA) and automate security based on alert. For example, a TCA can be defined for ACL deny count and if the ACL deny count exceeds a threshold, the end-point can be put into a suspect category and more closely monitored by:
- Inserting advanced security service for traffic from suspect end-point (e.g., NGFW, IPS)
- Mirror select traffic from suspect end-points
These new capabilities enhances powerful security policy automation features already in VSP Platform for provisioning both workload centric security policy as well as enterprise wide policy enforcement using on templates. In addition, Nuage VSP provides the ability to define an ACL sandwich that provides network security control over enterprise wide Infosec policies to ensure compliance while providing an option for network security teams to give application teams the ability to specify application specific whitelist policies for microsegmentation.
Related: If you missed our online presentation as part of Network Field Day 12 in August, we unveiled our new security automation capability. You can see an 18 minute demonstration of the new security capability that has put us at the forefront of thought leadership in the Software Defined Security category here.
Read the full PCI Compliance report here.
Read how Nuage Networks has integrated Palo Alto Networks as a security partner in our SDN overlay here.
Learn more about our security architecture for microsegmentation here.

